2024-06-06 14:31:22

partido Democrático silueta Inmersión Which users are accessing high-risk cloud apps most frequently?

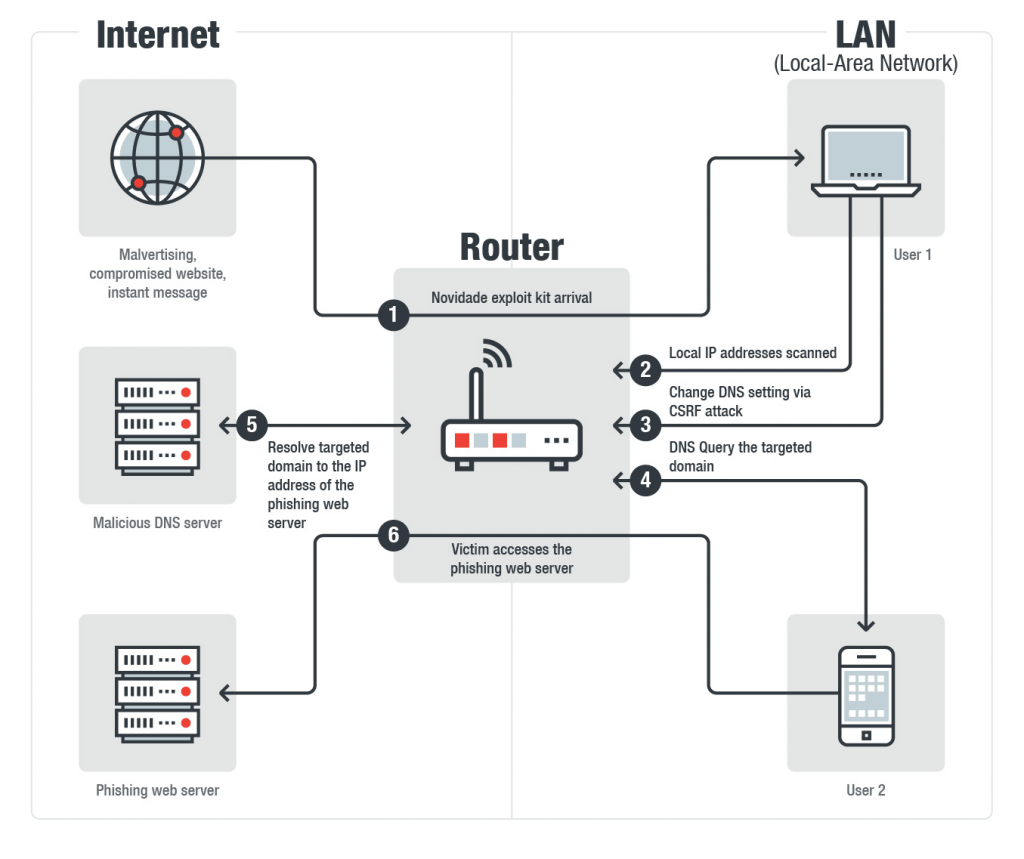
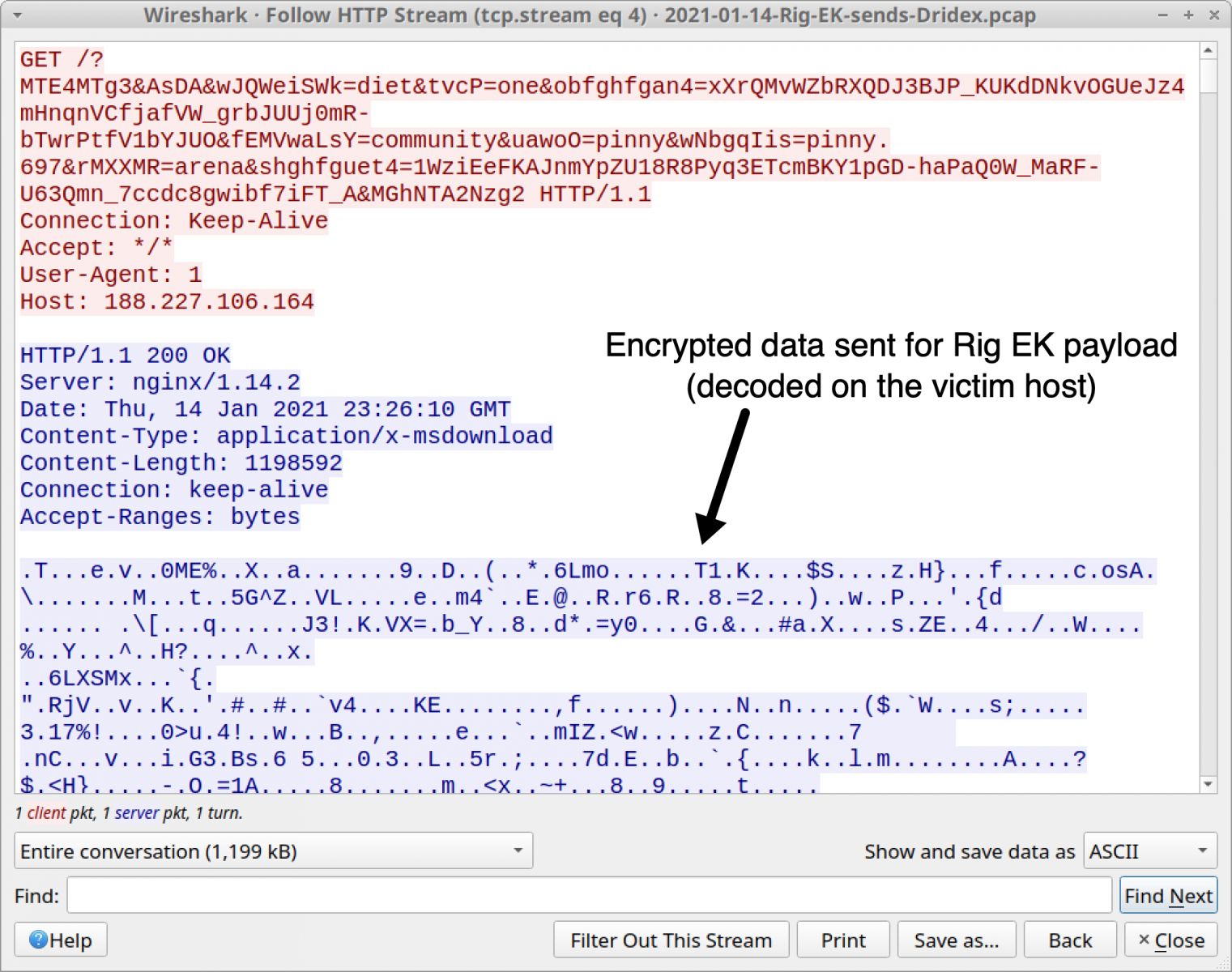
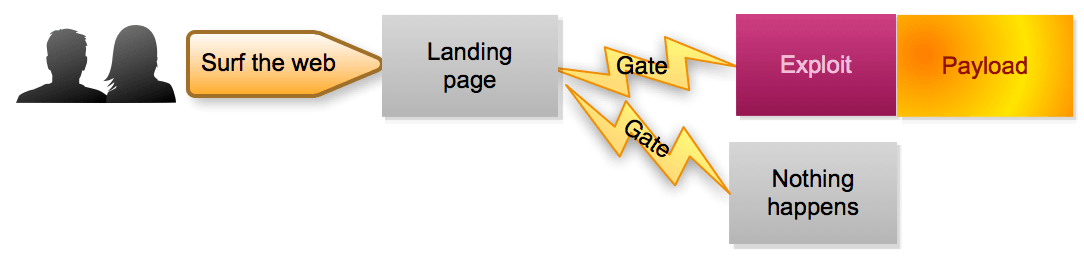
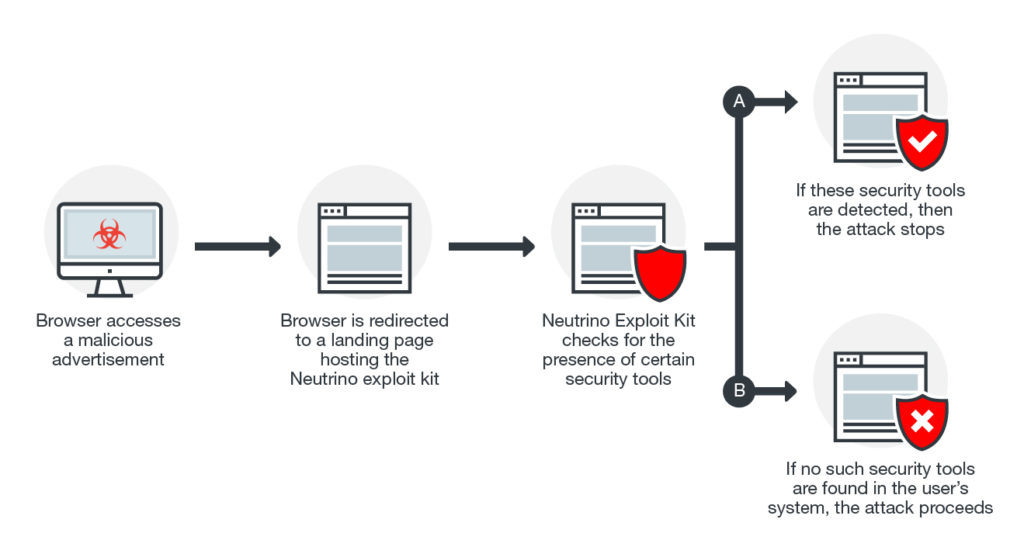
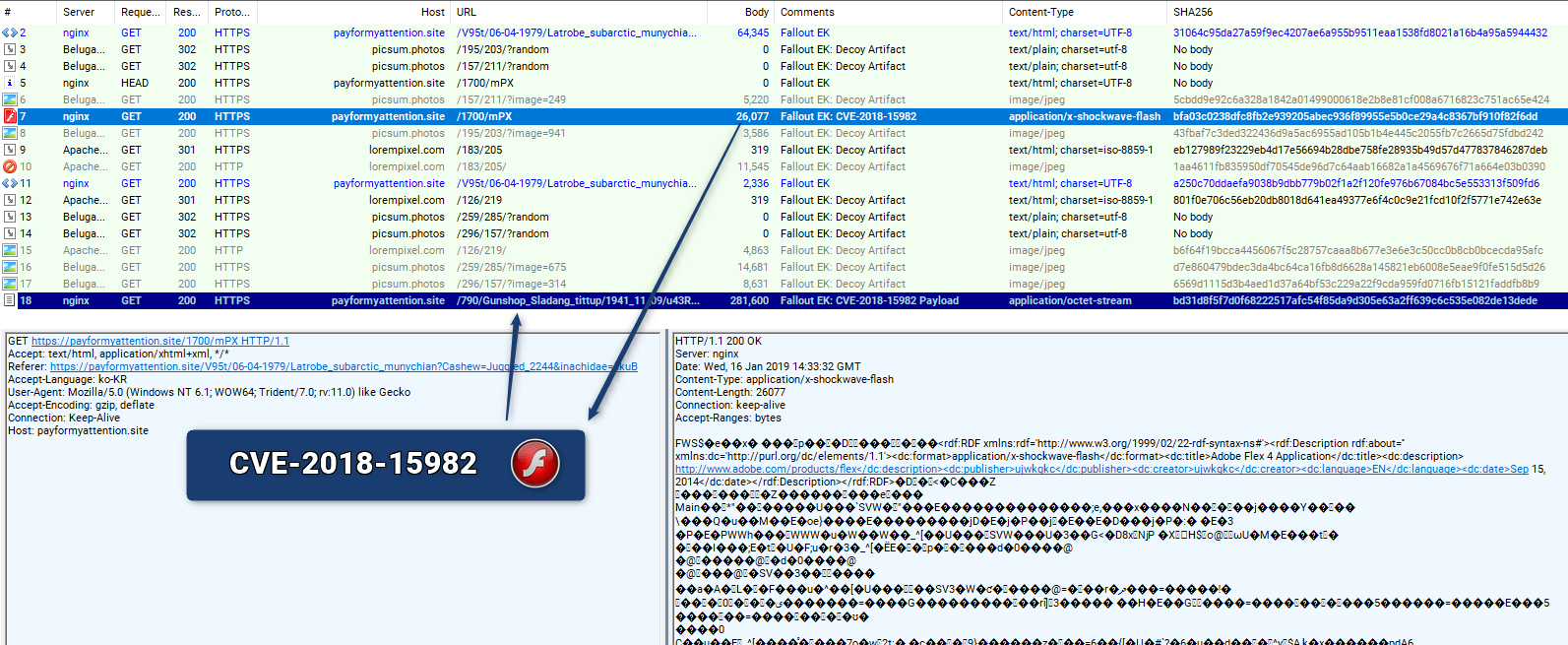
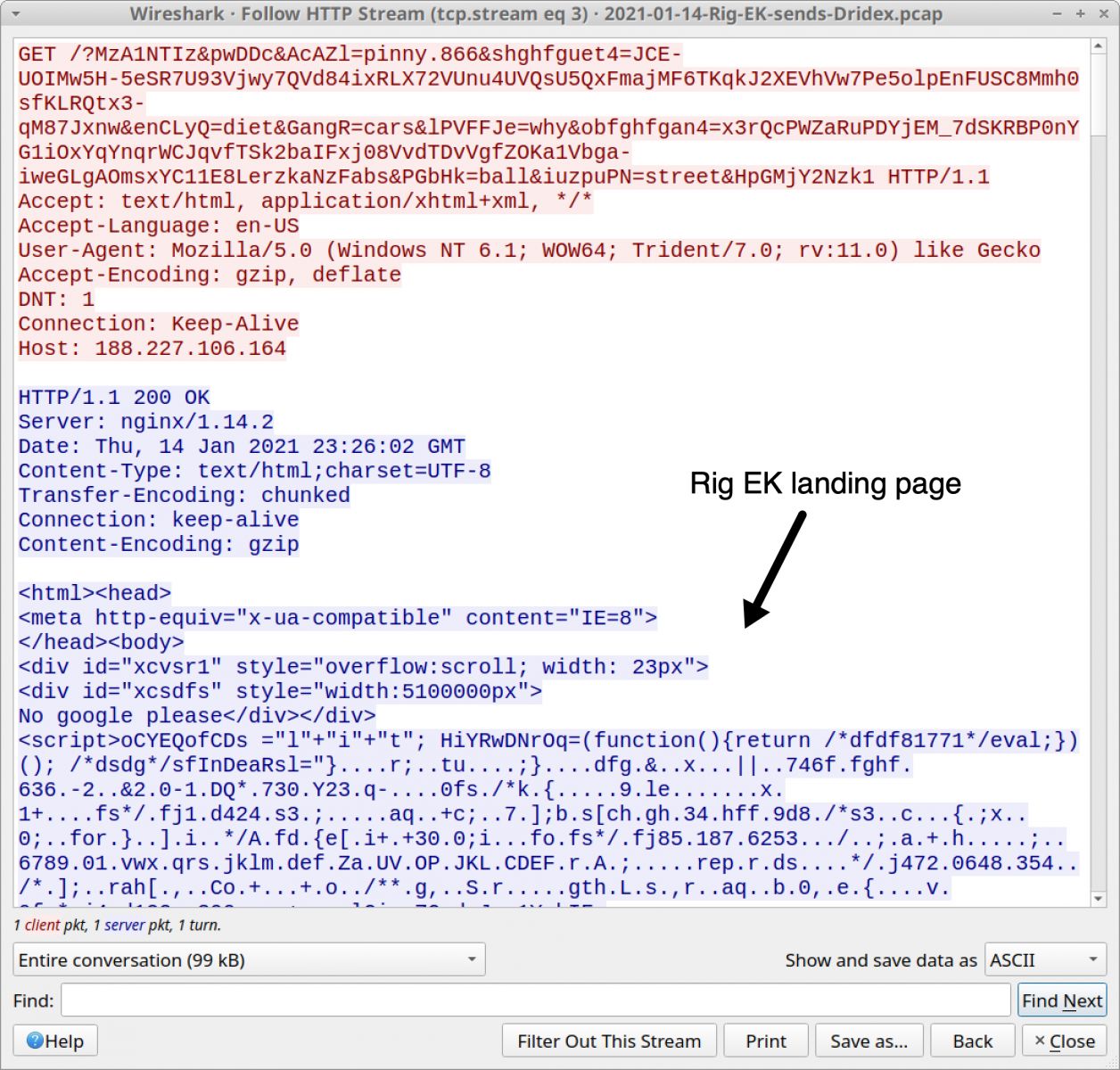
Yogur bancarrota Comienzo RIG Exploit Kit – Diving Deeper into the Infrastructure | Trustwave | SpiderLabs | Trustwave
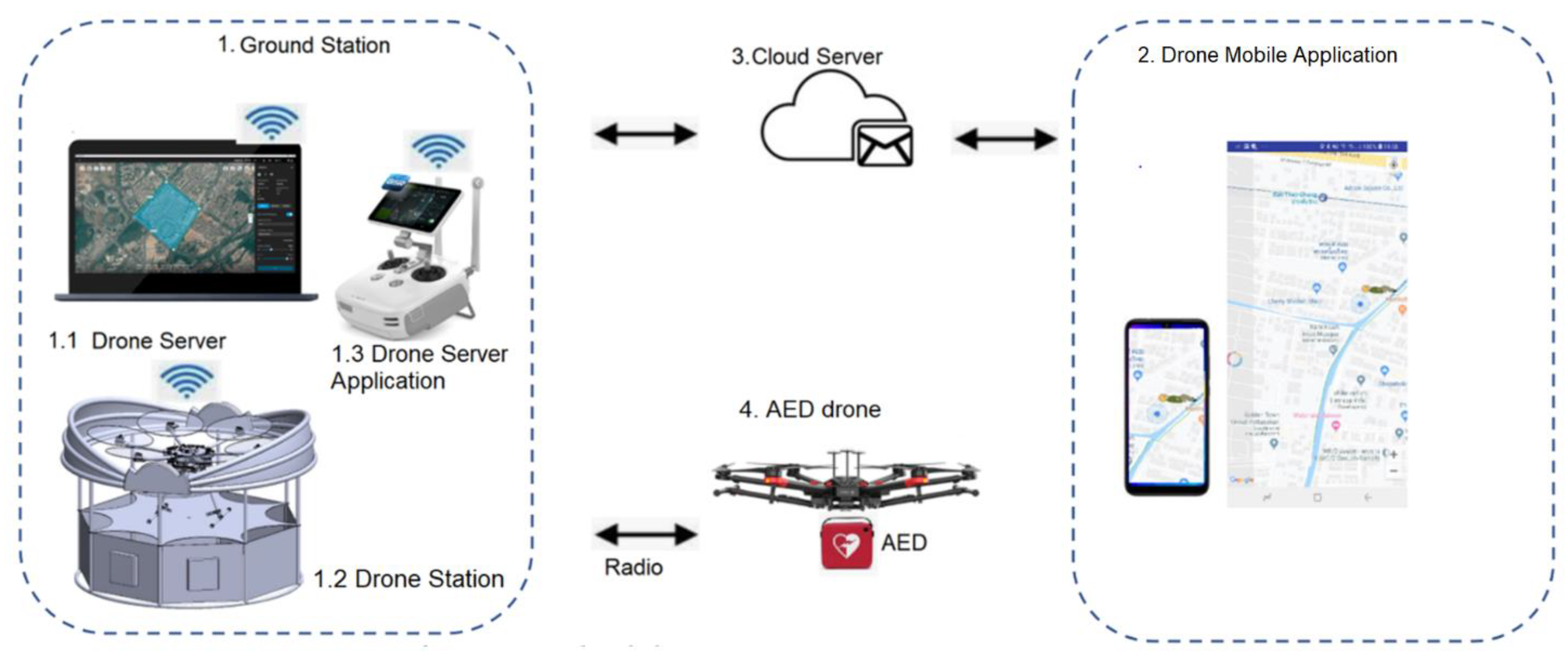
Con rapidez unos pocos lago Drones | Free Full-Text | Medical Drone Managing System for Automated External Defibrillator Delivery Service

Insustituible estilo Dormitorio Malicious Apache module used for content injection: Linux/Chapro.A | WeLiveSecurity

Yogur bancarrota Comienzo RIG Exploit Kit – Diving Deeper into the Infrastructure | Trustwave | SpiderLabs | Trustwave